Last late April a friend of mine had his iPhone stolen in the streets—an unfortunately familiar occurrence in big, metropolitan areas in countries like Brazil. He managed to buy a new one, but kept the same number for convenience. Nothing appeared to be out of the ordinary at first—until he realized the thief changed his Facebook password.
Fortunately, he was able to recover and update it, as his phone number was tied to his Facebook account. But a pickpocket accessing his victim’s Facebook account is quite unusual. After all, why would a crook be interested with his victim’s Facebook account for when the goal is usually to use or sell the stolen device? It didn’t stop there; a day after, my friend curiously received a phishing SMS message on his new phone.
What’s interesting here is the blurred line between traditional felony and cybercrime—in particular, the apparent teamwork between crooks and cybercriminals that results in further—possibly more sophisticated—attacks.

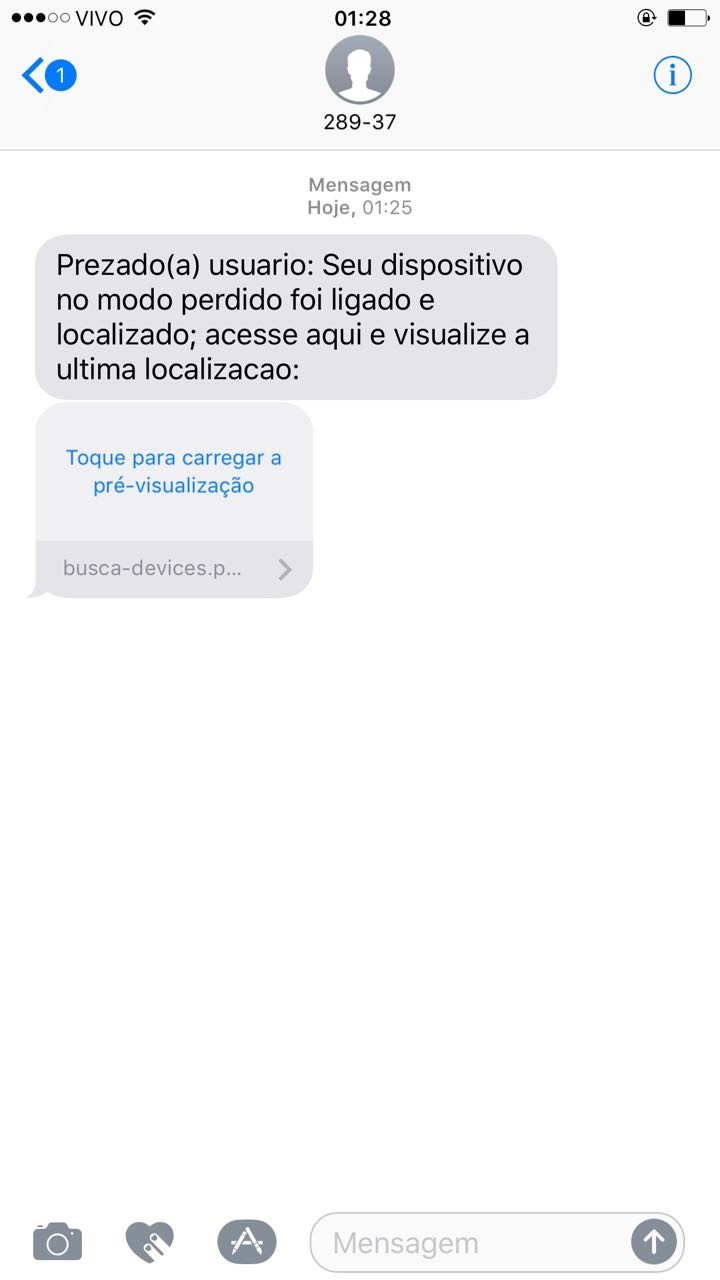
Figure 1: SMS message with a link to a phishing page
The SMS message, written in Portuguese, translates to: “Dear user: Your device in lost mode was turned on and found; access here and view its last location:”. The message was accompanied with a link pointing to hxxp://busca-devices[.]pe[.]hu, which we found to be a phishing page with a log-in form asking for Apple ID credentials.
We then checked the last location of his stolen iPhone, the official iCloud website indeed confirmed that it was where he had the phone snatched.

Figure 2: Phishing page asking for Apple ID credentials
Connecting the dots, it appears the modus operandi is to physically steal the victim’s phone (while in use, so they can still access the apps), uncover the device’s number, then try changing the password of installed social networking (and possibly email) apps—probably to extort the victim in the future—before turning the stolen device off as soon as possible. Attackers then try to grab the victim’s Apple ID credentials using a phishing page and a socially engineered SMS message pretending to be Apple. Apart from perpetrating identity theft, getting their hands on Apple credentials allows them to disable the Activation Lock feature in iOS devices which would enable them to wipe the phone (as part of an attack, or for them to reuse the device).

Figure 3: iCloud phishing page advertised in the Brazilian underground
Interestingly, we came across an iCloud phishing page peddled for R$135 (roughly equivalent to US$43 as of May 4, 2017) during one our recent forays into the Brazilian underground. The phishing page offered for rent came with a video tutorial explaining how the service works. Coincidence? While there may be no direct correlation, it wouldn’t be surprising if it somehow intersects with my friend’s iPhone scam situation—given how Apple credentials are one of the commodities sold in Brazil’s online underworld. In fact, this kind of attack has been reported in Brazil as early as 2015
Lessons Learned
The moral of my friend’s story? Traditional crime and cybercrimes are not mutually exclusive and can, in fact, work together in seemingly bigger attacks or malicious schemes. Another lesson learned? Physical security strengthens cybersecurity. This rings true—even intuitive—not only to individual end users. Organizations understand that the risks of attacks are just as significant if their workplace’s perimeters aren’t as properly secure as their virtual/online walls.
Indeed, today’s increasingly intricate—and in a lot of cases, brazen—attacks, whether physical or in cyberspace, call for being more proactive. Being aware of red flags in phishing scams, securing the privacy of mobile apps, and adopting best practices for BYOD devices, are just some of them. These are complemented by physically securing mobile devices—from password-protecting important documents to employing biometrics or strong PINs to prevent unauthorized access to the device’s apps.
Users can also benefit from multilayered mobile security solutions such as Trend Micro™ Mobile Security for Apple devices (available on the App Store) that can monitor and block phishing attacks and other malicious URLs. For organizations, especially those that use BYOD devices, Trend Micro™ Mobile Security for Enterprise provides device, compliance and application management, data protection, and configuration provisioning, as well as protect devices from attacks that leverage vulnerabilities, preventing unauthorized access to apps, as well as detecting and blocking malware and fraudulent websites.
With help from our colleagues from PhishLabs, we were able to take down the phishing pages that were still online. We also disclosed to Apple our findings related to this threat. The domains we uncovered related to this scam are in this appendix.