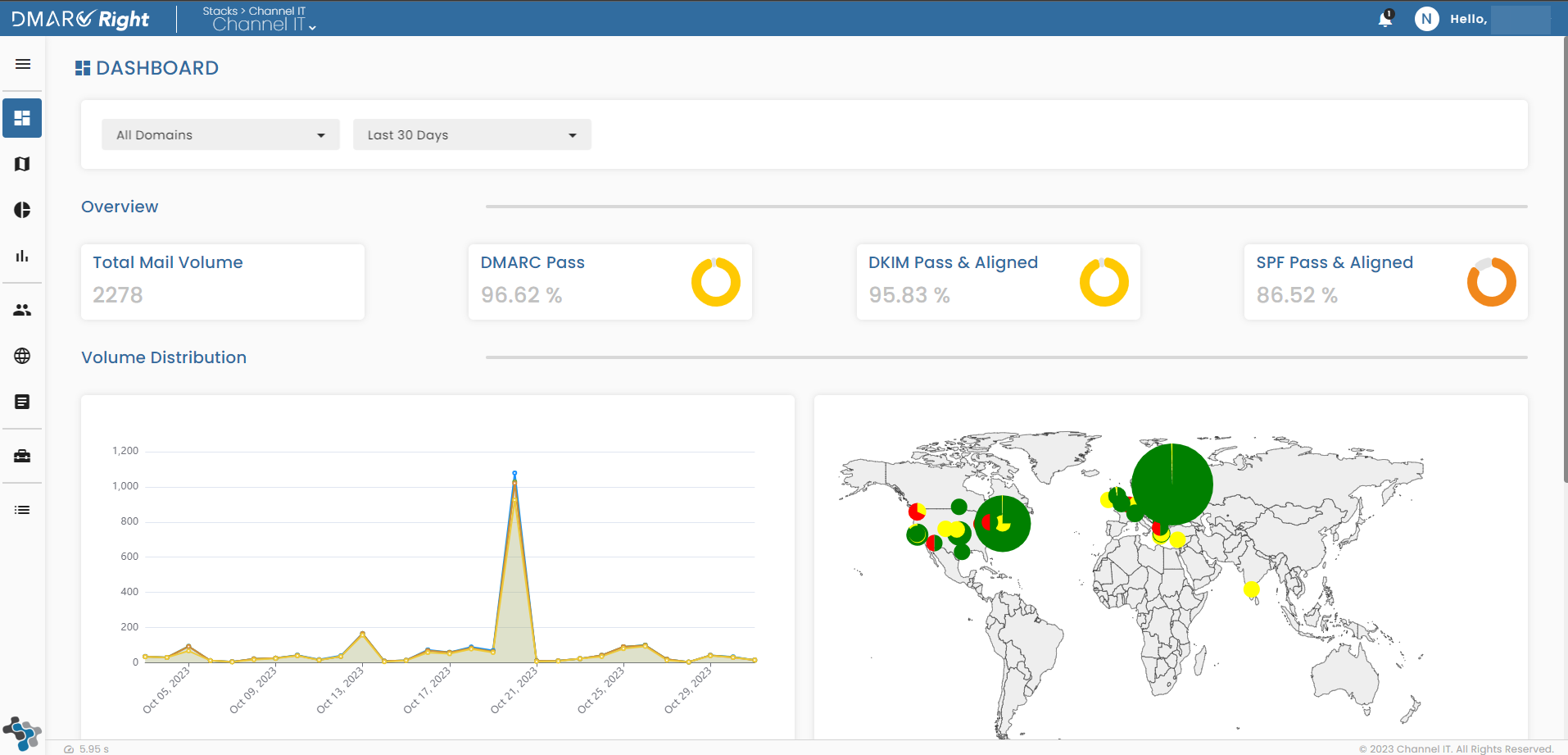
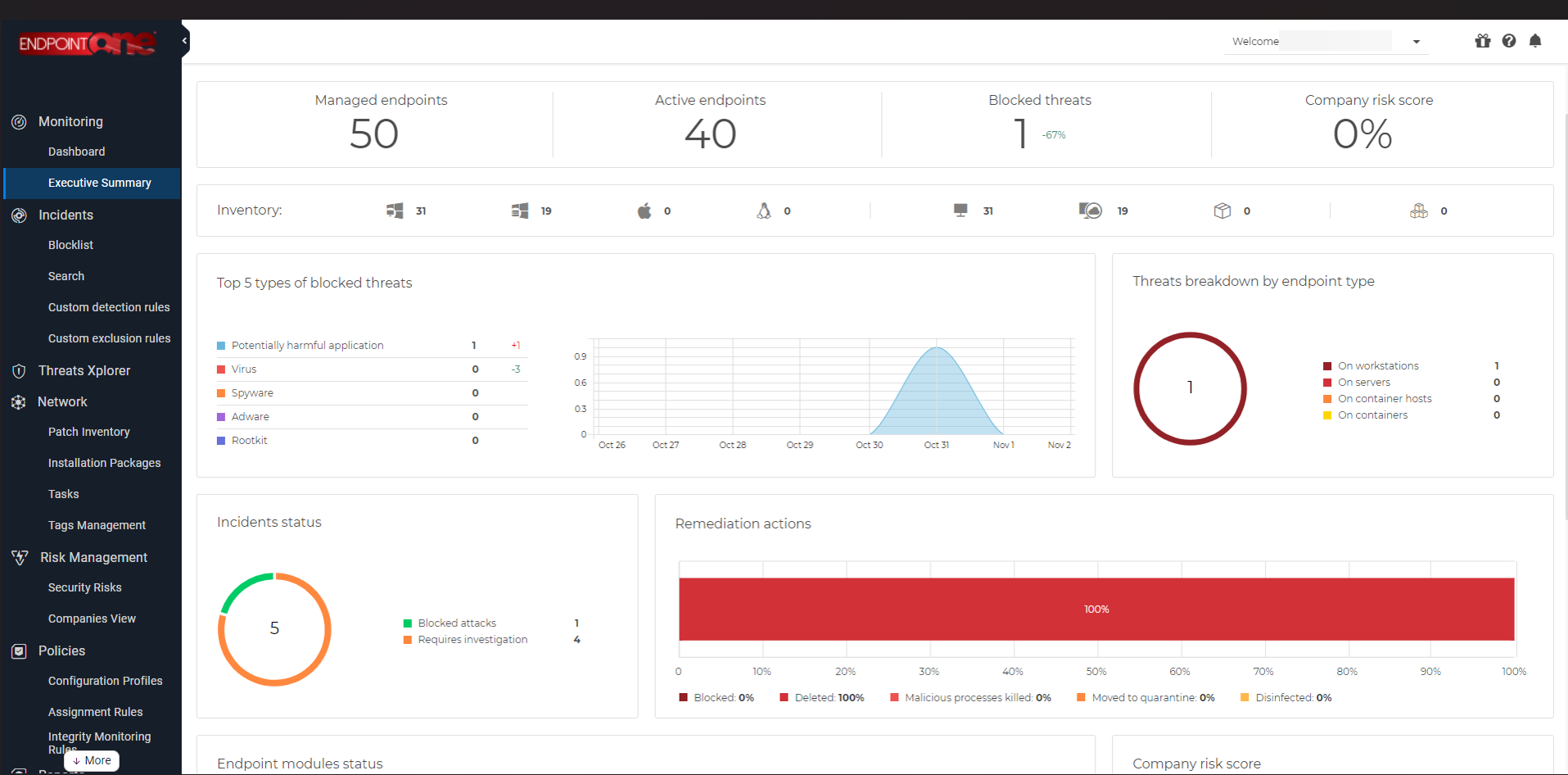
About Us
Channel IT Ltd. has transformed from its inception as a training and consultancy provider, to emerge as a leading Value-Added Distributor with Professional Services. Our strategic shift into a software developer underscores our commitment to providing comprehensive and tailored IT solutions for all business needs.
Our Partners
Channel IT Ltd. is bringing a unique partner-enablement program that is packed with resources, such as live demos, documentation for presentation and deployment, collaterals for all the solutions, case studies, training, constant guidance and unparallel support.
By entering our partner program, you unlock a world of opportunities in the Information Technology industry. Seize the chance to grow your business, enhance your portfolio and create mutually beneficial relationships between your organization and your customers.
0
+
Years of Experience
0
+
Innovative IT Products
0
+
Unique Customers
0
+
Unique IT Projects